Secure Open Source Software Is Helping Enterprises Find Their Edge
While businesses are benefiting from open source software, security needs to be tightened. Here's how the Open Source Security Foundation is helping to make open source secure.
May 20, 2022

As organizations seek to gain an edge over their competitors, they are finding power in open source, which has led to, in the words of Brian Behlendorf, GM of the Open Source Security Foundation, a "Cambrian explosion" of open source. But with the rise in use of open source code has come a rise in vulnerabilities and so a need to better secure open source software.
During his "The Power of Open Source" presentation at this month's MIT Technology Review Future Compute conference held at MIT's Cambridge, Massachusetts, campus and in an interview with ITPro Today, Behlendorf highlighted the growth of open source and the security challenges that come with that growth.
According to Sonatype's 2021 State of the Software Supply Chain Report, he said:
There are currently over 40 million open source software components available.
There will be 420 million open source software component releases available by 2026.
Developers are downloading 2 trillion open source packages a year.
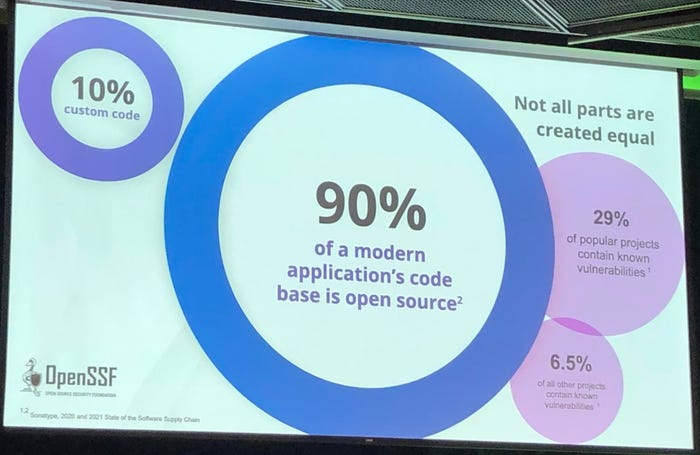
The debate about open source code versus proprietary code has largely gone away, according to Behlendorf. "Very rarely are developers or enterprises making a binary choice between the two," he said. Studies have found that 90% of an average application stack is pre-existing open source code that has been pulled together and assembled, with about 10% of that as the custom code.
"Defining your edge is really about getting that 10% right and aggressively covering the rest of the 90% with the free stuff that you can find pre-existing," he said.
open-source-software_0
Vulnerabilities in Code Are on the Rise
There is a problem, however, according to Behlendorf: There's a blind spot in the open source space — and the software space as a whole — to the rise of vulnerabilities in the underlying code.
"I wake up in the morning and fire up my laptop … and get that notice, 'Hey, there are updated packages. Do you want to update this before you start your day?'" he said. "And I always get that dopamine hit from clicking 'yes,' partly because I know that that means that to reasonable concern I'm protected against the threats that somebody might want to throw at me today."
In the same vein, organizations need to be ready to update, Behlendorf said. "How do we get enterprises to get to the point where they go for that same dopamine rush that I do when I wake up in the morning and hit 'update' on my laptop?" he asked.
What's troubling is that, according to Sonatype, 29% of the popular open source projects contain known vulnerabilities in either the core code or in their underlying dependencies, Behlendorf said. Some of these vulnerabilities are easy to exploit, like the one recently discovered in the Log4j logging library. The Log4Shell exploit became a poster child, he said, to the point where the U.S. government asked those involved in the open source industry: "Are you OK over there? How did you not catch this?"
To help prevent such exploits, the Linux Foundation in 2020 formed the Open Source Security Foundation, which Behlendorf heads. OpenSSF, which raised $11 million in what is essentially yearly memberships, focuses on improving the state of cybersecurity in the open source space supply chain, he said.
OpenSSF is looking into the question: The way code is built in the software industry — and not just open source code but the supply chain that we have in software — are there vulnerabilities that are starting to affect that? We need to get smarter about closing some of those opportunities for exploit, he said.
How Software Bill of Materials Can Help Secure Open Source
One of the tools to address this is something that the White House has elevated in importance. In May 2021, Executive Order 14028 was issued to improve cybersecurity. The order calls for, among other things, a Software Bill of Materials (SBOM) to be included with every software package delivered to executive branch agencies. Behlendorf compared an SBOM to the ingredients label on a bag of bread, as it enables organizations to see exactly what they are getting.
OpenSSF is looking at how to use SBOMs ubiquitously across software supply chains and get them integrated into core code as well as upstream. As developers write and release software, they will also provide SBOMs, including ingredients that came from previous software "so when an enterprise has to go out and address a remediation, they at least know where they're vulnerable, and that's the beginning of figuring out how to remediate for that work," he said.
OpenSSF is addressing a number of ways to secure open source software.
"This is not about writing the one tool that that automatically improves all of our cybersecurity," Behlendorf said. OpenSSF is about:
Prioritizing, identifying and securing the most critical projects.
Automating the tools that developers use to see whether their code is secure or to pick more mature platforms.
Educating developers on how to think like an attacker and choose patterns that will lead to better quality code.
Funding fixes for the most critical projects. Sometimes someone needs to step up, Behlendorf said, and say, "Here's the forgotten package way down in the stack that is actually ubiquitously used everywhere" and actually write the code and cover the last mile.
Informing stakeholders where the risk is across their whole portfolio of code.
Pushing standards for the signing of code for traceability through the supply chain.
"Open source is everywhere, and you've got to figure out how to make use of it," Behlendorf concluded. "But it really is about figuring out, how do you define your edge to be that layer on top and get really good at taking advantage of what's come before us?"
About the Author(s)
You May Also Like




